Cybersecurity: Utilities Working to Maximize Opportunity, Limit Vulnerabilities
The annual Black & Veatch 2019 Strategic Directions: Electric Report survey found that driven by a rapid increase of digital transformation from the back office to field networks and devices, the power industry is transforming with new opportunities that are improving operational efficiency, productivity, and resiliency across the electricity value chain. But such connectivity and change come with the weighty risk of heightened network exposure to cyberattacks and the sector may not be adapting its risk management approaches quickly enough to manage the dangers associated with the pace of digital change.
As we are continuously enabled and spurred on by new levels of digitalization and the internet of things (IoT), cybersecurity postures are coming under intense scrutiny by security professionals, regulators, the federal government and utilities, who have seen firsthand how pervasive — and crippling — cyberattacks can be. The memory of the Ukrainian 2015 cyberattack still is fresh in the minds of cybersecurity professionals after hackers managed to shut down the Ukrainian power grid, causing outages across the country.
Considering observable threat-analysis trends, U.S. industry professionals expect cyberattacks to increase in frequency and sophistication. Illicit individuals and maligned anonymous groups will continue to develop cyberweapons capable of disrupting operations, damaging equipment, and compromising sensitive data. A 2018 study by financial services group KPMG found that nearly half of power and utility executives (48%) expect a cyberattack to be inevitable.
Utility leaders know they are at a crossroads as they scramble to balance technological opportunity with safety and security, all the while willing to put capital behind their investments. As utilities invest more in the distribution grid and distributed energy resources (DERs), turn more consumer-centric, and the IoT becomes the norm for customer engagement and interaction, utility leaders view cybersecurity processes, procedures, governance, technology, and overall threat management as an industry top concern.
Polling illustrates that. According to the Black & Veatch 2019 Strategic Directions: Electric Report survey of the North American power industry, respondents asked about the most challenging issues facing electric utilities ranked cybersecurity third, behind aging infrastructure and an aging workforce. 92% said they plan to invest in beefing up the security of their data and internal systems.
Cybersecurity’s Weakest Link
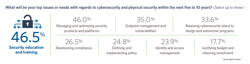
Most electricity providers manage their security needs in-house, making it no surprise that respondents identified security education and training as the top need in managing organizational cybersecurity and physical security.
Implementing security education and training will help bring utilities into compliance with North American Electric Reliability Corp. (NERC) critical infrastructure protection (CIP) requirements, which mandate that electric utilities have cybersecurity training programs in place to mitigate human error — the weakest link in the cybersecurity chain. For example, phishing emails — a type of online scam in which malicious actors use what appears to be an email from a legitimate company to steal sensitive information — remain a scourge to cybersecurity teams. The solution is simple: don’t open untrusted emails and don’t click untrusted email links. The most advanced threat models include the fact that some — a very small portion of the population — always will click unsafe links despite warnings against it. Therefore, information technology (IT) professionals must install back-end email protection systems that can disable or remove unsafe links to mitigate the inevitable human error.
In the Black & Veatch survey, managing security products and platforms was identified as the second most important need. Respondents prioritized endpoint management (mobile devices, PCs, laptops, and so forth); vulnerabilities management; retaining cybersecurity talent; maintaining compliance with NERC-CIP requirements; defining and implementing cybersecurity policies, guidelines and procedures; identity management; and access management. Justifying budgets and investments was the final priority our respondents identified.
Access Control Still a Sizable Vulnerability
According to survey data, more than one-quarter of respondents named access control as the biggest vulnerability in ensuring cybersecurity and physical security. When it comes to access control, there’s the physical act of letting someone into the facility, which is typically governed by background checks, risk assessments, and permissions-based badging. And there’s logical access, which allows permissions-based access to remote and networked systems, and is controlled through user-level authentication controls, two-factor authentication, and even advanced technologies such as biometrics.
From there, survey respondents prioritize risk assessment, identification and authorization, incident response/contingency planning, asset management, and configuration management. Surprisingly, respondents ranked asset management fifth on the list, even though it is among the most critical points because organizations cannot protect what they don’t know they have. Asset management is a prerequisite for a good, holistic cybersecurity program, and organizations cannot employ effective cybersecurity without effective asset management. Utilities are starting to build comprehensive operational technology (OT) cybersecurity enhancement programs that complement and further enhance the security and defense capabilities of OT systems, and asset management is foundational to ensure complete coverage and compliance.
Managing Supply Chain Risk
So looking ahead, where does this leave the industry with regard to cybersecurity? CIP 013-1 will become enforceable in mid-2020, meaning energy companies will be required to adopt security controls that mitigate supply-chain risks such as malware exposure and backdoor accesses directly onto our sensitive networks and equipment. Supply chain cybersecurity requirements, mature supply management and patch management, traceability requirements are recommended steps that can mitigate threats inherent in manufactured systems with digital components.
When it comes to ensuring supply chain risk management, security-in-depth is the best practice. Know your manufacturer. Know the manufacturing process, leveraging trusted foundries with complete control over the manufacturing process and chain-of-custody controls.
On the opposite — and most dangerous — end of the spectrum, equipment is manufactured overseas in unknown factories, using unknown chipsets and firmware. This untrusted equipment often is assembled piecemeal, with parts coming from everywhere, using software that has no visibility or control. This frequently is the case when OT equipment is bought off a department store shelf, or worse, a foreign super-discount internet site that may sell counterfeit OT devices. Such untrusted devices introduce risks of malware when connected to sensitive networks.
The middle of the spectrum (and most practical) is to use well-known and trusted suppliers who abide by published and auditable supply-chain security programs.
Best-of-brand OT suppliers have established physical security at all facilities, logical security for production systems, production certifications, a strict scrap handling process that prevents counterfeiting protection labels, and security technology such as smart chips and security labels that prevent unauthorized tampering.
In the end, cybersecurity defense for OT is a journey that requires focus, dedication, and executive management commitment to really change the culture and raise the level of competency across the organization. Consistent governance and an agile approach to stay ahead of threats will be key to managing the increasing risks of cyberattacks.
Part 1 in this four-part series addressed utility company wish list in planning for the distributed grid. Part 3 and 4 will address, "DER marketplaces: How Utilities Can Find Their Place?" and "Big Customer, Big Losses? Why Utilities Need More Customer Focus."