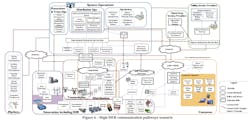
5G technology has implications at different levels of utility and OT systems. The main three being big data management, operating procedures and processes, and cybersecurity.
To effectively model an environment where 5G technology will be deployed, the National Institute of Standards and Technology (NIST) Smart Grid Logical Model is one of the best references.
It identifies several domain areas, including markets, operations, utility service providers' customers, transmission, distribution, and generation. It is essential to consider all the different actors that exchange information and the connections among them. The networks shown in the figure above must be considered as shared resources among different actors. Thus, high requirements in terms of guaranteed bandwidth and cybersecurity level must be requested to network providers to satisfy all the actors' needs. So while a large amount of data will be acquired, the interaction among different actors, systems, and security levels must also be considered. To build a trust chain that covers all the domains is of crucial importance.
The availability of sensors that can be used for sharing and exchanging the acquired information among different domains and actors implies a change also on the telecommunications network and systems for data ingestion. In the past, functional units would often select a communication means suitable for a specific application. This resulted in a siloed approach that frequently created a set of means that were either inconsistent or limited in capability.
Therefore, the potential of IEDs must be evaluated from the very beginning to project a system that can exploit this potential for both telecommunication networks and data ingestion systems. This brings to light the future capability needs of communications systems, the need for standardization and optimization, and the oversight that is required to harmonize the eventual convergence of IT and OT.
Proper actions have to be put in place to do it — OT people know process needs and data potentiality; IT people should help OT people find proper IT solutions in terms of applications, databases, cyber protection, and so on, to satisfy these needs. In some cases, the solution can be driven by IT; in other cases, like for standardization, the contribution of OT is crucial. OT people should evaluate if the IT solution could have drawbacks on the normal operation of the system (especially in terms of availability and integrity). While IT people should recommend the use of proper IT solutions, they should also assist in the selection of edge sensors to avoid what the sensors' lacks could reflect on the system, especially in terms of vulnerabilities. In the cybersecurity arena, the security level of the entire chain depends on the security level of the weakest link in the chain.
Utilities and related critical infrastructures have been the subject of multiple and varied cyberattacks. The data stolen from companies seem to be aimed at mapping critical infrastructures and collecting detailed information about them to create databases. If not adequately detected and contained, cyberthreats (advanced persistent threats or APT) can go on for a long time and impact networks, plants, monitoring systems, and information related to employees. It is worth highlighting that only a part of these have been properly investigated in the last few years. The stolen data makes it possible to reconstruct the operating criteria of companies, exposing them to even greater risks. Most of the time, the attacks are aimed at obtaining information rather than causing blackouts on the network. However, this information can be used in the future for targeted attacks.
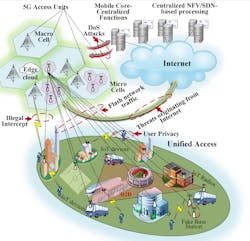
In such a highly connected environment, 5G introduces new technologies and devices that can create new risks, strictly connected to the new technology (for example, enlarged exposure surface, number of connected devices, and shared network resources). On the other hand, it increases the likelihood of existing threats because new access points (IED, IoT devices, and so forth) can be exploited to get into OT systems.
The Security by Design principle states: "If security is not projected from the beginning, surely there will be problems." This principle is essential, and for OT systems, Security by Design implies 'Resilience by Design' — OT systems must be able to respond and recover the full availability in a short period of time. Because a zero-risks condition does not exist, an efficient resilience should be projected from the very beginning to protect OT systems. Moreover, cybersecurity implementation and updates are needed because OT systems are affected by a legacy problem (large majority of industrial equipment are based on legacy infrastructure).
Finally, the introduction of communications networks and systems of systems, while enabling great functional interoperability, also exposes a potential for new threats. If we consider that pervasive wireless networks unlock a potential for a significant number of end-devices, most of which will be addressable, managing the credentials and limiting access introduce a significant need for device management and coordination. Without safeguards and communications management, such devices could, in fact, easily flood the network and create an inadvertent DoS because of congestion and not because of a cyberattack. Likewise, communication network security must be managed, especially over airlinks.
In conclusion, to exploit at best all the opportunities offered by 5G technology, it is crucial to face its introduction with a holistic approach. This implies involving all levels of utilities to create synergy among actors of smart grid, to harmonize IT and OT requirements and needs, and, last but not the least, to consider cybersecurity a key factor to deploying efficient and resilient OT systems.
In this respect, CESI Group (a world leader in technology and innovation for the power sector) is committed to research and applying various means of digitalization to its global customers.